Introduction
On June 21, 2021, the Ministry of Industry and Information Technology (MIIT) issued a draft of the “Guidelines for the Construction of Network Security Standard System for Connected Vehicles (Intelligent Connected Vehicles)” and solicited public opinions. At the same time, MIIT also released the “Instructions for the Preparation of Guidelines for the Construction of Network Security Standard System for Connected Vehicles (Intelligent Connected Vehicles)”. Hereafter, they are referred to as “Guidelines” and “Instructions” for convenience.
Two days later, on June 23, 2021, MIIT issued a draft of the “Notice on Strengthening the Network Security of Connected Vehicles (Intelligent Connected Vehicles)” and solicited public opinions. Hereafter, it is referred to as “Strengthening Work”.
The publication of two such documents in one week reflects the country’s emphasis on the development of intelligent connected vehicles in the “New Four Modernizations” and the importance of implementing network security work. The “Instructions” and “Guidelines” were published by the Technology Department of MIIT, focusing on the construction of the entire standard system for network security of intelligent connected vehicles. The “Instructions” answered more questions about “why to do it”, while the “Guidelines” answered more about “how to do it”. The “Strengthening Work” was issued by the Network Security Administration of MIIT and primarily answered the question of “who should do it and what should be done”.
In order of publication, let’s first look at the updated “Strengthening Work”. The underlined portions in the following text are direct quotations from the original document.
Strengthening Work
Who Should Do It?
The opening of the “Strengthening Work” clearly identifies the target audience:
“Industrial and Information Technology Departments, Communication Management Bureaus of provinces, autonomous regions and municipalities directly under the Central Government, China Telecom Group Co., Ltd., China Mobile Communications Group Co., Ltd., China United Network Communications Group Co., Ltd., and relevant connected vehicle operation enterprises and intelligent connected vehicle production enterprises.”
The scope of the target audience is comprehensive. For those in the automotive industry, the focus is on connected vehicle operation and production enterprises, which are required to fulfill the network security related work mentioned in the “Strengthening Work”.
What Should Be Done?
The “Strengthening Work” systematically elucidates the focus of the network security work for intelligent connected vehicles:
- Strengthen the network security protection of connected vehicles (V2X).
- Strengthen the platform security protection.
- Ensure data security.
- Strengthen security vulnerability management.
The first point emphasizes the security of connected vehicles (V2X), including network facilities, communication security, security monitoring and early warning, emergency response, and protection level filing. Among them, the security monitoring and early warning require monitoring traffic and behavioral patterns through relevant technical means to ensure security, while the corresponding preserved network logs require a retention period of no less than six months. In addition, emergency response requires regular emergency drills to promptly deal with network security risks. This makes me think of “security invasion exercises” similar to fire drills, which may come into view in the future. If so, car makers will certainly be participants in this type of exercise, but I don’t know if ordinary drivers will also be required to participate?## English Version:
Let’s start with the second point. Platform safety includes access management of network platforms, OTA security, and application program security of intelligent connected vehicle APP. From this, we can see that “OTA” and “software ecosystems” that are often used as selling points on car sales terminals will have better network security management.
The third point, data security, includes data management regulations and technological guarantee capacity. A key emphasis is placed on safety management of data export. For instance, map information, geographic information collected by sensors, face information, etc. on many foreign auto brands produced cars will also receive better management according to this point.
The fourth point, safety vulnerability management includes management mechanisms, capability building, and coordinated response. It clearly stipulates that when vulnerabilities are discovered or learned in network facilities, business systems, and intelligent connected vehicle products of the enterprise, remedial measures shall be taken immediately and vulnerability information shall be reported to the network security threat and vulnerability information sharing platform of the Ministry of Industry and Information Technology.
This article defines that enterprise-side vulnerability information must be synchronized with the information on the Ministry of Industry and Information Technology platform.
In the “Guide Construction Preparation and the Guide” article, the background and necessity of constructing guidelines are elaborated. Among them, the following paragraph stood out: “The connected car technology is a new business format that combines the next generation of network communication technology with the automotive, electronics, transportation, and other sectors. It is one of the main vertical applications of 5G communication technology and infrastructure for a new network that achieves connectivity between the car, the road, the cloud, and the network. With the development of the connected car industry, network attacks increasingly spread to the vehicle-end and connected car platforms, and network security incidents not only affect citizens’ privacy, property, life, and safety but may also threaten social and national security. Starting from the key links and focal objects of the intelligent connected vehicles, the V2X communication network, the connected car service platform, the connected car application program, data protection and other key areas, it is imperative to build a network security standard system for connected vehicles (intelligent connected cars), exert a standard-leading role, and support the safe and healthy development of connected cars.”
Two key points can be noted from this:
- The connected car technology is one of the main vertical applications of 5G communication technology. The country is expected to promote the development of connected cars.
- Network security incidents of connected cars will not only affect citizens’ privacy, property, and life safety but may also threaten social and national security. These are critical issues where money is not a solution, and it is of utmost importance to address such a “bottleneck” problem in terms of personal, property, and national security.
Finally, the “Guide Construction” elaborates on the system construction of intelligent connected vehicle network security standards, from general requirements to construction ideas, and specific construction contents are discussed comprehensively. The construction idea chapter presents the following technical architecture.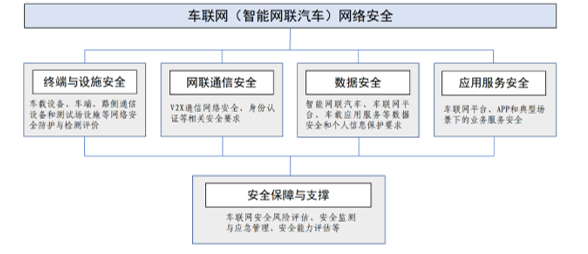
This is closely related to the focus of “strengthening work”. The construction content section explains the content of the network security standard system in detail and in a hierarchical manner. The following figure is the framework diagram of the system, which is divided into three layers. In the “Construction Guide”, a more detailed and specific standard catalog, namely the “Fourth Layer” further refined, is also attached.
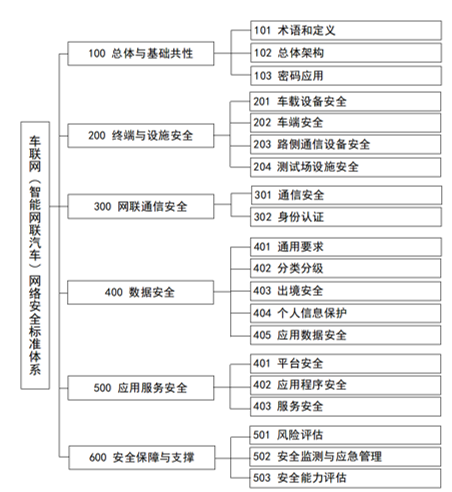
Among them, the ones that are more directly related to the technical development of intelligent connected vehicle production enterprises are “201 Vehicle Equipment Security” and “202 Vehicle Terminal Security”. These standards cover communication, diagnosis, application functions, as well as software, operating systems, hardware, chips and other aspects.
Many times we encounter a question: “If the network security of the vehicle gateway is done, is it unnecessary to do it for other vehicle nodes?” From these two parts, “201 Vehicle Equipment Security” and “202 Vehicle Terminal Security”, we can see that the answer is negative. The network security of intelligent connected vehicles is a systematic project, and even within the vehicle scope, the system design of each controller and each part is required.
Engineers in the automotive industry can consider further development in these directions. Entrepreneurs and investors can also aim at the direction and concentrate their efforts. It is believed that as China’s intelligent connected vehicle development becomes more and more advanced, the development of network security can also make synchronous progress.
Reference:
-
“Construction Guide for Network Security Standard System of Connected Vehicle (Intelligent Connected Vehicle)” (Draft for Soliciting Opinions)
-
Compilation Instructions for “Construction Guide for Network Security Standard System of Connected Vehicle (Intelligent Connected Vehicle)” (Draft for Soliciting Opinions)
-
Notice on Strengthening the Network Security of Connected Vehicle (Intelligent Connected Vehicle) (Draft for Soliciting Opinions)
This article is a translation by ChatGPT of a Chinese report from 42HOW. If you have any questions about it, please email bd@42how.com.
