*Author: Neo Wong
Introduction
With the rapid advancement of modern electronic, communication, and sensing technologies, the electrification level of automobiles has become increasingly high. However, this has also introduced information security risks. HEAVENS is considered an excellent information security risk assessment model in the automotive industry, but its assessment workload is large and relies on sufficient time and strong professional ability.
To solve this problem, this paper proposes to use BP neural network to generate a neural network model, which is used to improve the HEAVENS evaluation calculation method to achieve the goal of saving time and manpower. Through simulation experiments, the method proposed in this paper can efficiently achieve security risk assessment.
Introduction
With the trend of communication technology and mobile internet applications, wireless communication vehicles have been introduced into the automotive industry, bringing about the emergence of smart cars and networked cars. While bringing a lot of technological innovation to the automotive industry, it also makes the automotive system increasingly complex [1].
Complexity means vulnerability. In recent years, there have been many events caused by automotive information security vulnerabilities, such as the remote control of Jeep by hackers in 2015 [2], the discovery that Nissan cars can control some important functions of the vehicle through defective APIs in 2016 [3], and the remote control of Tesla’s braking system by Tencent KeenLabs through diagnostic interfaces [4] in 2017, and so on.
In order to overcome the information security problems faced by automobiles, the automotive industry has invested more and more energy. The second edition of ISO-26262 released at the end of 2018 proposed guidance on the interaction between functional safety (Safety) and information security (Cybersecurity) [5]; ISO-21434 released in 2020 provides guidance on the implementation level based on SAE J3061, which guarantees the implementation of automotive information security engineering in risk assessment management, product development, production/operation/maintenance, process review and other aspects, and requires automotive and affiliated product information security to achieve a common understanding of security in product development and design throughout the supply chain [6].
Risk assessment management plays a key role in automotive information security, affecting the subsequent work process.”HEAVENS” is an abbreviation for “HEAling Vulnerabilities to ENhance Software Security and Safety project”, a European proposed method, process and tool support for threat analysis and risk assessment of vehicle electronic and electrical(E/E) systems. It is a structured and systematic method for discovering potential threats. However, one of the shortcomings of HEAVENS is that it requires a lot of evaluation and calculation when conducting TARA (Threat Analysis & Risk Assessment), which consumes a lot of time and manpower.
To address this issue, this paper proposes a method of using BP neural network to generate neural network model parameters and then improving the risk assessment algorithm of HEAVENS with the generated model. This method can achieve efficient risk assessment results while saving time and manpower required for evaluation. Through simulation experiments, the method proposed in this paper is reliable and effective.
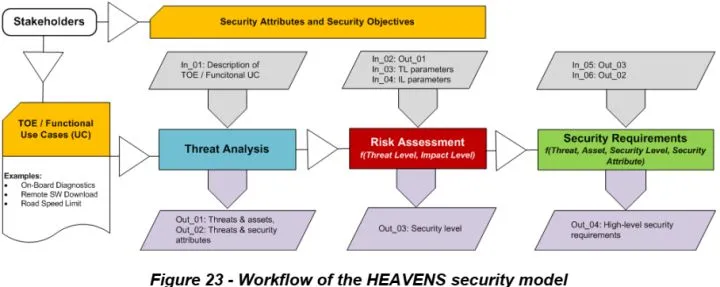
HEAVENS Security Model evaluates Security Risks
HEAVENS Security Model proposes a systematic method for deriving information security requirements of automotive E/E systems. Considering the most advanced threat analysis and risk assessment methods, it adopts three steps to analyze security requirements, as shown in the figure below:
- Threat analysis
HEAVENS security model uses the STRIDE method [8] proposed by Microsoft to conduct threat analysis.
STRIDE is a structured and qualitative security method used to discover and enumerate threats that exist in software systems. However, the applicability of the STRIDE method has been extended to automotive electronic and electrical systems. Microsoft Threat Modeling Tool can be used to draw data flow charts and automate STRIDE threat analysis.
- Risk assessment
After analyzing the “threat-asset” (Threat-Asset) pairs based on the STRIDE method, a security level is evaluated for each TA pair. Risk assessment includes three steps:


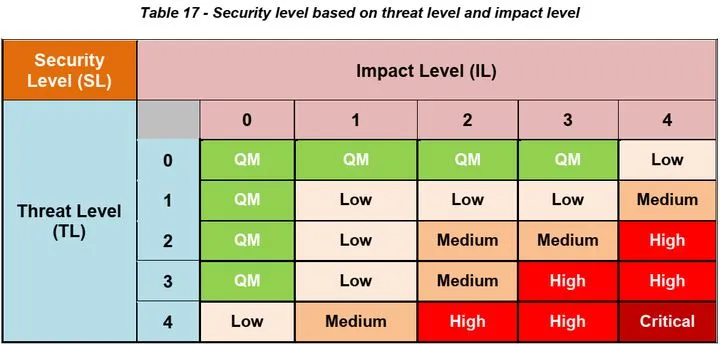
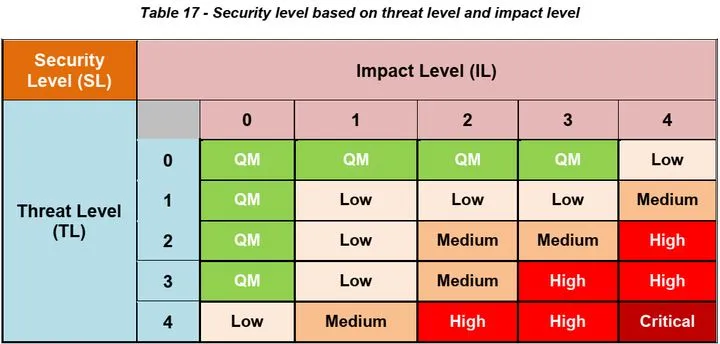
3. Determination of Security Level (SL)
The Security Level (SL) corresponds to the final risk rating, which is determined jointly by the TL and IL.
- Security Requirements
The last step is to derive security requirements based on the Asset, Threat, security attributes, and SL. When an Asset has a security level of “QM”, it may or may not require additional information security requirements. If it is not “QM”, information security requirements should be established for the other two cases.
HEAVENS benefits from the steps and methods of STRIDE, making it possible to discover potential threats in a structured and systematic way. However, this requires a lot of work to analyze and determine the IL and TL factors of individual threats and thus determine the SL. The calculation method can be illustrated using Figure 2.

Based on the analysis of HEAVENS above, it can be seen that the large number of parameters and the reliance on expert evaluation result in a tremendous amount of work.
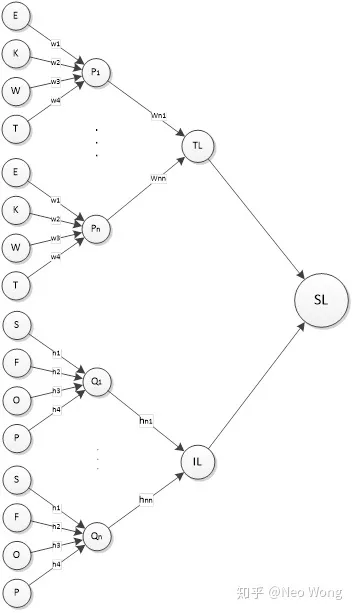
Improving the HEAVENS Assessment Calculation with BP Neural Network Method
BP Neural Network is a method of calculating, analyzing, and predicting using information and data. The neural network has a very strong ability to extract features from data, and thus, neural networks combined with BP Neural Network have made breakthroughs in fields such as speech/image/text recognition, robots, and biomedicine. This demonstrates that the adaptability of “data + neural network” is very strong.
Because the HEAVENS security model requires a lot of work and expert evaluation to calculate the numerous information security threats faced by automotive systems, efficiency is low, and misjudgments or omissions of security risks are common. Therefore, the application of “BP Neural Network + Neural Network” to improve the HEAVENS calculation method should be able to solve these problems and improve the efficiency of security analysis, thus enhancing the information security level of automotive products.Because the values of TL and IL are determined by a series of parameter vectors, it is suitable to use BP neural network for processing. In this paper, two multi-input, single-output, one-hidden-layer BP neural networks are constructed for calculating TL and IL respectively. Then the obtained TL and IL values are used to calculate the final SL value.
- Calculation of TL
Design TL as a BP network with n * 4 inputs and 1 output.



- Calculation of IL
Design IL as a BP network with n * 4 inputs and 1 output.

- Calculation of SL
The calculation parameters of TL and IL will be trained based on a large amount of data. After the training is completed, TL and IL will be used as the calculation parameters of SL to obtain the risk assessment value based on the method shown in Table 3.
The improved calculation methods for TL, IL, and SL in HEAVENS can be represented by Figure 4.

Application Examples
The experimental data in this paper comes from a total of 47,441 TA pairs, and 1,035 TA pairs of safety evaluation data for a BCM are selected.
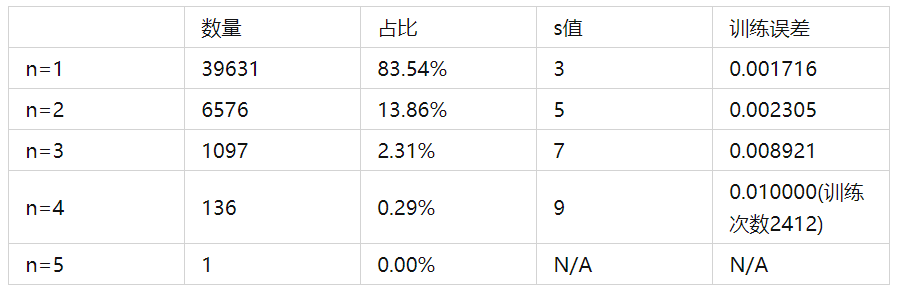
When calculating the SL of the whole vehicle, the values of n and m for TL are as follows:

The values of n and s for IL are as follows:
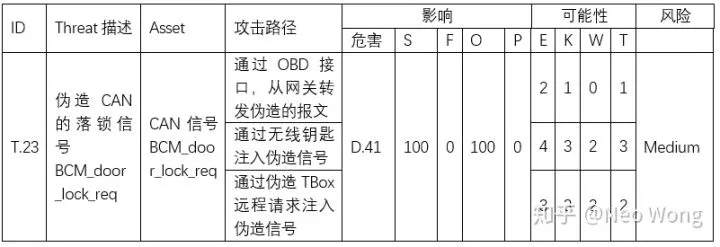
 The following example illustrates the calculation of a BCM’s TA. The table below shows the original security assessment table:
The following example illustrates the calculation of a BCM’s TA. The table below shows the original security assessment table:
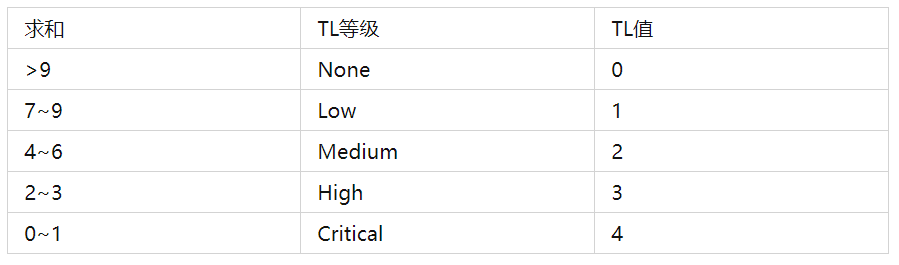
After training the model, TL is calculated with n=3, IL is calculated with s=1, and the decimal part of the calculation result is rounded to the nearest integer. The calculation result is as follows:

According to the mapping in Table 3, the value of SL can be obtained as Medium, which is consistent with the expected value.
The following shows the TL verification deviation when calculating BCM’s SL based on the completed training network:
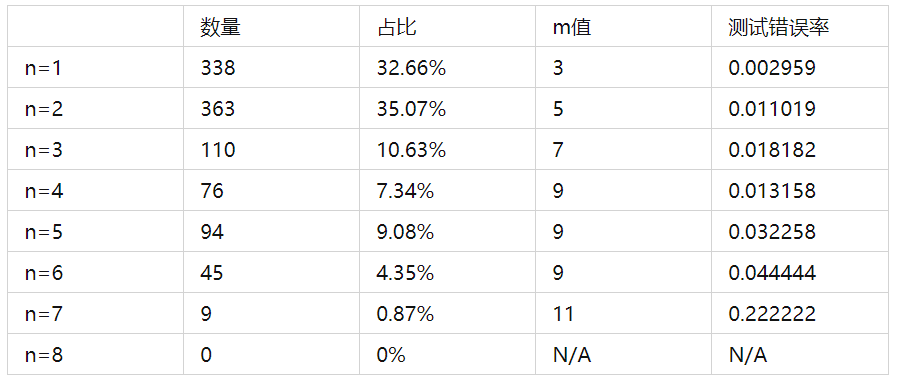
The verification of IL is as follows:
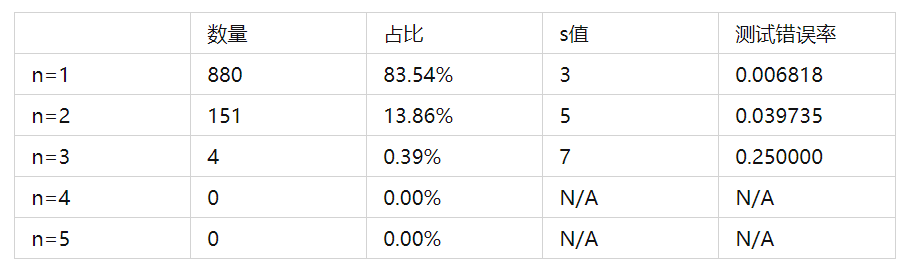
From the above calculation results, it can be seen that when using a large number of training samples to generate network parameters, the calculation results of the improved HEAVENS model based on this article’s method are consistent with expert evaluation results, which has the advantages of quick calculation and high accuracy.
Conclusion
This article proposes a method based on BP neural networks to generate model parameters for the car safety risk assessment results. The TL and IL calculation methods of the HEAVENS model have been improved, and the BP neural network model is used to calculate the information security risk level of different factors. After simulation verification, this method has a high degree of automation, effective and efficient evaluation results, and can provide computational support for quantifying and assessing automotive information security risks.
This article is a translation by ChatGPT of a Chinese report from 42HOW. If you have any questions about it, please email bd@42how.com.