Smart Car and Network Security
The development of smart cars and the Internet of Vehicles has led to the emergence of the automobile network security industry. Over the past decade, with the acceleration and development of electronic and information technology, smart cars have transformed from a concept to a reality. In people’s minds, traditional cars are still a means of transportation that expands travel range. However, smart cars have already begun to be transformed into mobile intelligent devices that users can ride on.
There are several basic properties that a car must possess to be called a “smart car”:
-
Automatic Driving Function: Smart cars are equipped with advanced sensors, high-performance chips, and other devices. They can detect the real-time traffic conditions on the road and use data processing systems and new technologies such as artificial intelligence to calculate and judge the vehicle’s driving status and road environment. The ultimate goal is to make smart cars fully autonomous.
-
Advanced Software Platform: The foundation of smart cars is the software platform system. Through the software platform, the vehicle can be connected to the network and updated with core functions to become an intelligent mobile space and application terminal. Smart car companies need to master all the software inside the car, especially the parts related to core functions, and constantly develop and iterate and push them to users – this evolution requires the car to have a complete and comprehensive software system.
-
Intelligent Cockpit System: Smart cars need an interactive system to be recognized and operated by users. The intelligent cockpit system needs to be able to support both manual and automatic driving modes. In either mode, smart cars need to have the ability to “perceive” and “understand” humans, and comprehensively judge users’ physiological status (such as facial features) and behavioral status (driving behavior, voice, and body behavior) through the analysis of perception data such as visual and auditory data inside the car, combined with biometric technologies such as face recognition and voice recognition, to ultimately achieve the goal of correctly manipulating the vehicle.
To achieve the intelligence of cars, the design of automobile electronic and electrical architecture needs to evolve from a distributed architecture to centralized domain controller architecture. For example, Volkswagen needs to introduce three ICAS (In-Car Application Servers, which are essentially three high-performance domain controllers) and a high-speed vehicle Ethernet and various other bus communication networks into the electronic and electrical architecture to form a more advanced architecture system. The service-oriented design of software and hardware separation makes this system have high computing power, high scalability, high portability, and upgradability, which can cope with the increasingly complex system complexity and rapidly respond to market demands.
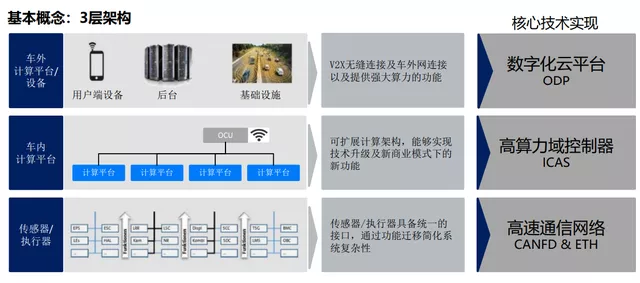
Automotive Network Security Technology
With the development of smart cars, vehicle safety must be considered from an overall perspective, and network information security products have also emerged.Why do smart cars need multiple network security products to protect connected vehicles? This is because vehicle networking security involves a wide range, including hardware network security, embedded network security software, and cloud network security platforms. Based on the three-layer architecture of “cloud”, “pipe”, and “end”, the vehicle networking under the network security perspective is shown in the figure below.
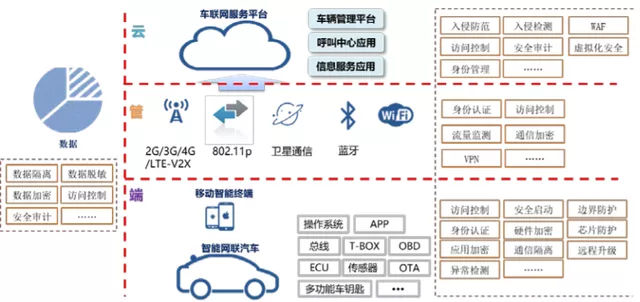
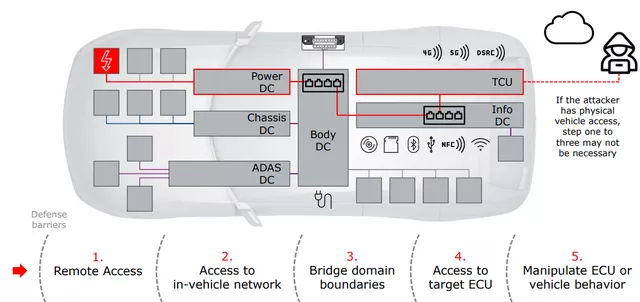
Hardware network security: Many MCUs used in electronic control units (ECUs) have built-in hardware to simplify and accelerate network security software. Secure hardware extension (SHE) adds on-chip hardware to any MCU. SHE is typically used with encryption keys to achieve better hardware performance and protection than software execution. Another example is the trusted platform module, which is used for secure key authentication, encryption, and decryption through a secure encryption processor. The third example of hardware reinforcement to improve network security is EVITA or E-safety Vehicle Intrusion Protected Applications.
Embedded network security software: In addition to hardware, security software is needed to protect most ECUs, especially those with wired or wireless connections. In most connected vehicles, ECUs with connectivity are called gateways and must have strong network security. Domain controllers can access many other ECUs and need their own network security hardware and software. Vehicles that communicate around the CAN communication in the serial bus are relatively vulnerable in terms of network security. Ethernet is relatively better deployed in terms of network security.
Automotive cloud network security platform: In the backend of smart cars, services are critical, and cloud network security provides real-time attack detection for connected vehicles and provides situational awareness for network health and threats. Data collection and analysis for identifying and improving network security cloud platforms are always running.
OEM Manufacturers and Network Security
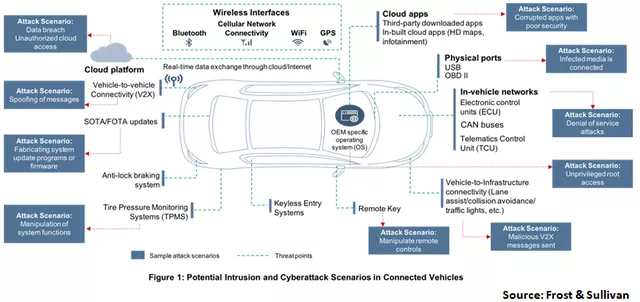
Most automakers did not initially consider designing more network security features for vehicles. Since 2016, events in the field of vehicle information security attacks have emerged, and most automakers have realized information security issues since then, and took action in 2018 to layout the automotive information security sector. With the UN’s attention, especially the publication of WP.29 regulations, more automakers have begun to take network security seriously. Automakers also gradually realize that network security is essentially as important as OTA.At present, domestic and foreign automobile companies are actively deploying automobile safety systems. With the increasing number of open-connection vehicles, the data exchange between related equipment and systems has become more and more closely linked. Internet security threats such as network attacks, Trojan viruses, and data theft have gradually extended to the automotive field. If the vehicle system, key components, or connected car platform are under network attack, it may lead to the vehicle being controlled illegally, which can cause privacy leaks, property losses, and even personal injuries. Network security has become the foundation and prerequisite for the healthy development of the connected car industry.
Network Security Solution Provider C2A Security
C2A Security is a trusted end-to-end automotive network security solution provider that has created a truly holistic method for in-vehicle network security. Its embedded network security solutions adopt a multi-level security approach, providing automotive-related protection and security compatibility. C2A’s network security lifecycle management platform, AutoSec, provides visualized management for vehicle manufacturers and tier-one suppliers, enabling them to meet the network security needs of the entire lifecycle of connected cars.
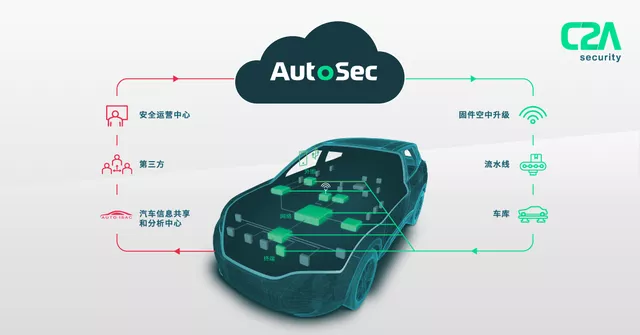
Founded in 2016, C2A Security has raised $6.5 million in venture capital to date. In October 2020, C2A released the first automotive network security lifecycle management platform, AutoSec. AutoSec provides three important capabilities that vehicle manufacturers and suppliers need: visibility, control, and protection.
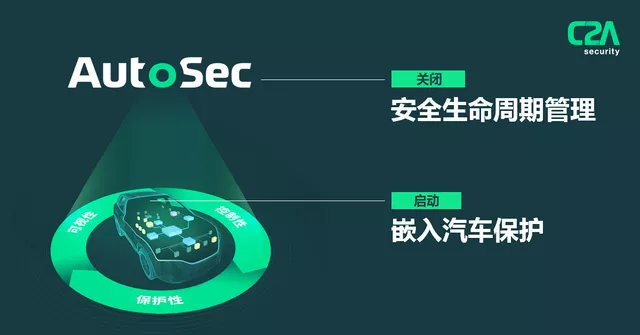
AutoSec’s unique orchestration platform provides manufacturers with unparalleled transparency throughout the network security lifecycle, optimizing management at each stage: risk assessment, plan determination, policy development, and policy execution. Vehicle manufacturers and tier-one suppliers simplify in-vehicle network security management, coordinate communication in the supply chain, automatically identify and block threats, and continuously evolve according to the needs of vehicles, protecting present and future connected cars. AutoSec makes it easier to comply with regulations, ensuring that vehicles comply with ISO 21434 throughout their lifecycle from the concept stage to product development and production.# C2A Security’s Automotive Cybersecurity Products Provide Real-time Protection for the Weakest Links in Vehicles: Peripherals, Networks, and Terminals
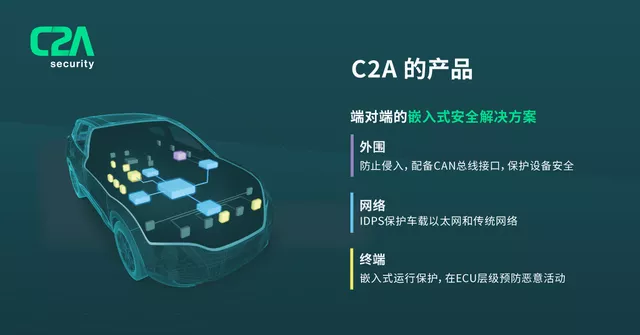
C2A has developed embedded network security products and a cybersecurity lifecycle management platform to address the critical importance of network security in the automotive industry. Created in collaboration with car manufacturers, this platform is tailored to the specific needs of the industry.
In April 2020, C2A joined AUTOSAR as a development partner. AUTOSAR is a global automotive platform alliance. C2A provides knowledge for developing embedded network security solutions to the automotive industry, enabling the industry to upgrade the network security standards faced by manufacturers and suppliers.
While many suppliers in the automotive network security market can provide protection for only one of the peripheral, network or terminal layers, C2A is the only supplier in the market that can simultaneously protect all three layers and offer a tailored cybersecurity solution through its advanced security lifecycle management platform.
This article is a translation by ChatGPT of a Chinese report from 42HOW. If you have any questions about it, please email bd@42how.com.