It was discovered by engineers that the control software of an SUV produced by a joint venture brand in China can be connected to at any time to obtain data such as throttle and brake pedal opening degrees, and these data will be transmitted in real-time to overseas servers through the app. This means that every action of the car executed by the owner through the app will be stored as data on overseas servers.
With the rapid development of the digital economy, global information enters the era of big data where comprehensive penetration, cross-border integration, acceleration of innovation, and leading development are taking place. Data is explosively growing, and the world is entering the era of data explosion. Data security has become the most important, complex, and challenging work in digital risk governance.
Against this backdrop, on June 10, 2021, the 13th National People’s Congress Standing Committee passed the “Data Security Law of the People’s Republic of China” (hereinafter referred to as the “Data Security Law”) by voting, which will be officially implemented on September 1, 2021. The formal promulgation of the “Data Security Law” after nearly three years of preparation marks that China finally has a fundamental law and an important law in the field of national security specifically for “data security”.
Before this, although there were relevant laws and regulations such as the “Cybersecurity Law of the People’s Republic of China”, the “Assessment Measures for the Security of Personal Information and Important Data Outbound (Draft for Solicitation of Opinions)”, the “Assessment Measures for the Security of Personal Information Outbound”, the “Personal Information Security Specification for Information Security Technology”, the “Assessment Measures for the Security of Personal Information and Important Data Outbound (Draft for Solicitation of Opinions)”, the “Action Plan for the Development of the Connected Vehicle (Intelligent and Connected Vehicle) Industry” and the “Personal Information Protection Law”, none of them specifically regulated the subject of “data”.
The “Data Security Law” is a law that coordinates “security and development” in the era of digital economy. Its promulgation marks the end of the era of data barbarism, and will also provide more guarantees for the development of the next stage of digital economy. The “Data Security Law” is formulated to regulate data processing activities, safeguard data security, promote the development and utilization of data, protect the legitimate rights and interests of individuals and organizations, maintain national sovereignty, security, and development interests.
In recent years, with the accelerated development of intelligent-connected vehicles, the issue of intelligent vehicle data security has become a key concern in the industry. The promulgation of the “Data Security Law” actively responds to the critical issues of data competition and protection at home and abroad, and provides guidance for enterprises’ compliance management of data operations as well as the development and governance of further data assets.
On the morning of June 11, 2021, the day after the promulgation of the “Data Security Law”, Tesla announced on Weibo that “data privacy and security concern every consumer. Tesla will strictly adhere to the Data Security Law to protect consumer data-related rights and interests, and make efforts to promote healthy and vigorous development of industries and the digital economy.”
Data Security of Smart CarsThe cameras, LIDAR, radar, speedometers, navigators, and other sensors, as well as various apps integrated into smart cars, are constantly collecting environmental, driving, and personal information on vehicles. Therefore, safety issues that used to exist with smart mobile devices will now also “transfer” to smart cars, and data security, personal information, personal safety, and public safety issues will also become “roadblocks” to the commercial use of smart cars.
Among them, data security will be the focus of legal attention, as the various data collections in smart cars pose a huge risk of leakage. Network security systems should be regarded as a standard feature of smart cars, just like seatbelts, and the mandatory testing of smart car network security should be promoted to strengthen the supervision of data security generated by intelligent connected vehicles. At the same time, the software supply chain of the automotive industry should be standardized, and the relevant laws and regulations and standards for data collection, storage, processing, and application of autonomous driving vehicles should be implemented as soon as possible.
A large amount of software on smart cars also involves domestic and foreign supply chain vendors, which need to be updated through over-the-air (OTA) technology. If past lessons cannot be learned, and excessive tolerance is given to “development first, governance later”, and the security management of the software supply chain is not standardized, and software security testing is not effectively implemented to minimize software vulnerabilities and Trojan horses, there will be huge risks to the functional safety and data security of smart cars, which may seriously threaten social security, even national security.
Data Types
What information and categories of data are included in vehicle data?
Vehicles involve many types of data, such as:
(1) Personal information of the vehicle owner, driver, passenger, etc.: such as name, age, occupation, mobile phone number, account, password, email, WeChat username, etc.;
(2) Vehicle data: such as license plate number, vehicle identification number, engine number, device number, etc.;
(3) Driving data: such as location and navigation information, driving tracks, vehicle control data, vehicle operating condition data, vehicle log data, vehicle driving data, vehicle environmental data. The most sensitive data that is easily involved mainly includes: flow data of people and vehicles in important sensitive areas such as military management zones, surveying and mapping data with precision higher than that publicly released by the government, operational data of the electric vehicle charging network, and vehicle type and flow data on roads, as well as external audio and video data such as faces, voices, and license plates.
(4) Other data: such as various permissions and app usage data collected through App, and data from car software (such as playlist and other preference information, home and company geographic location information).
The diversity of vehicle data makes its legality and compliance a complicated issue. Different types of data correspond to different legal obligations, requiring different compliance measures. The collection and processing of different types of data not only provides more convenience and safety for our driving, but also poses challenges to privacy and personal information.
Data Security and Data Export ControlHigh-level intelligent driving cars have powerful data collection capabilities. For example, a smart driving test vehicle can generate up to 10TB of data per day, mainly consisting of the geographical information collected by the vehicle sensors during mapping behavior. In principle, such information can only be collected by licensed organizations. However, some of the sensitive geographical information data is not stored domestically and can be easily exported abroad, especially for multinational car companies like Tesla.
Tesla’s in-car system can collect data that can be scanned by mapping, including street conditions, navigation distances, and environmental scenery, which are mainly stored on foreign servers. Some of this data contains geographical information. Once leaked, it may jeopardize social or national security. Therefore, concerns have been raised about Tesla’s data collection, upload, and security issues in China.
Tesla can collect more than 200 pieces of information covering personal information of car owners, vehicle environmental information, vehicle driving information, and car owner cellphone information, while domestic counterparts collect more than 170 items. If such a large amount of information falls into the hands of independent commercial companies and is misused, it may result in great risks to social and national security, especially if the information is related to key individuals’ personal or behavioral information, real-time environmental information obtained by vehicle-road collaboration, sensitive geographical location, etc.
In March 2021, Tesla CEO Elon Musk responded to vehicle data security concerns for the first time, stating that the company would not provide the US government with data collected by its vehicles in China or other countries. He also emphasized that Tesla customers’ data in China would receive adequate protection, and Tesla had a very strong motivation to keep any information confidential.
However, this response did not eliminate concerns of Chinese users. As autonomous driving and new energy vehicles become more and more popular, more and more data is being collected and stored. Many experts believe that legislation to regulate the safety of autonomous driving data should be enacted as soon as possible.
On May 25, 2021, Tesla’s official Weibo account announced that the company had established a data center in China to achieve localized data storage and would gradually increase more local data centers. All data generated by vehicles sold in the Chinese mainland market would be stored domestically.
Tesla also announced it was developing a vehicle owner data platform, which will be open to owners so they can query and access real-time data. This work is currently underway in full swing. It is worth noting that Tesla owners in North America can currently apply to download their own driving data.
In accordance with Chinese regulations, users have the right to access their driving data. While Tesla establishes a data platform, it should appropriately address data security issues such as restrictions on non-data subjects’ access and defense against hacker attacks and tampering.Currently, there are no standards applicable to the construction of intelligent connected vehicle data platforms, and each intelligent connected vehicle builds its own data platform. Data platforms need to meet different levels of information security standard requirements according to their different characteristics. For data platforms with strong confidentiality, level three information security protection is the basic requirement. There are already intelligent connected vehicle data platforms that have referred to the level three information security protection standard.
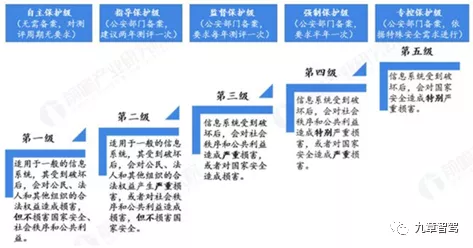
Therefore, it is urgent to add a “lock” to the data of intelligent connected vehicles. Relevant laws, regulations and standards for data collection, storage, processing and application need to be implemented more quickly. Constrained types and ranges of data collection need to be strengthened, especially for intelligent cars that collect a large amount of personal and environmental information. It is required that they comply with national laws and standards, and the collected data of vehicle owners, environmental data and road network data should follow compliance and usage principles, and over-collection must be avoided.
For some data that must leave the country, the government should set a quota limit on the amount of data, and the critical core data must be kept in China, while the other data may need to be reviewed before being allowed to leave.
Data Security and Personal Information Security
An engineer once analyzed the control software code of an SUV produced by a certain brand’s joint venture in China and found that the App could communicate with the vehicle at any time and obtain data such as throttle, brake pedal opening and closing degree, and these data would be transmitted to overseas servers in real time. This means that every action performed by the owner on the vehicle through the App will be stored in the form of data on overseas servers.
Domestic joint venture automakers focus on manufacturing localization, but they do not do a good job of localizing data analysis in the vehicle development process. Most of the data collected by sensors are sent to overseas R&D departments for analysis.
Article 37 of the “Cybersecurity Law” stipulates that “the operator of key information infrastructure shall store the personal information and important data collected and generated during the operation within the territory of the People’s Republic of China.”
In fact, before this, a series of regulations and policies (drafts for soliciting opinions) on data security and data exit have already been issued:
On April 11, 2017, the National Internet Information Office drafted and published the “Measures for Security Assessment of Personal Information and Important Data Exiting the Country” (draft for soliciting opinions), which stipulates in Article 2 that the personal information and important data collected and generated by network operators in China shall be stored within the territory of China. If necessary to provide data offshore, a security assessment should be conducted according to this method.The ninth provision states that “network operators shall report to industry regulators or supervisory departments for a security assessment on outbound data that contains or accumulates personal information of 500,000 or more individuals, data volume exceeding 1000GB, and information related to nuclear facilities, chemical biology, national defense industry, population health, large-scale engineering projects, marine environment, and sensitive geographical information.”
On June 13, 2019, the Cyberspace Administration of China issued the “Personal Information Security Assessment Measures for Cross-Border Transfer” (draft for comments), stating that “network operators who provide personal information collected within the territory of the People’s Republic of China to overseas entities shall conduct a security assessment in accordance with these measures. If the security assessment confirms that the outbound of personal information may affect national security or harm public interests, or cannot effectively ensure the security of personal information, the outbound shall not be permitted.”
If we assume that personal information and vehicle data have already been collected, what car owners are more concerned about is whether intelligent connected vehicles will “lock” their data after the information has been collected.
Recently, Volkswagen stated that the personal information of about 3.3 million Volkswagen and Audi car owners and potential customers had been leaked. Specific information includes name, address, mobile phone number, email, and some driver’s license numbers, license plate numbers, and loan numbers. Information leaks in automobile companies are not uncommon. Network security experts have said that automobile companies need to have more comprehensive management and control over the storage, use, and transmission of data.
On June 11, 2021, a supplier notified Mercedes-Benz of a data breach. Mercedes-Benz immediately launched an investigation and released preliminary results, stating that after evaluating 1.6 million data samples, it found that less than 1,000 people’s personal information was publicly accessible. The affected individuals are customers and potential buyers who input sensitive information on Mercedes-Benz and dealer websites between 2014 and 2017. This information includes personal credit scores, a small number of driver’s license numbers, social security numbers, credit card information, and dates of birth.
Mercedes-Benz stated that there is currently no evidence suggesting that this information has been maliciously misused. The company is contacting the affected individuals, and “any individual whose credit card information, driver’s license number, or social security number has been leaked will receive 24 months of free credit monitoring.” Mercedes-Benz also stated that it will notify relevant government agencies and ensure that the supplier will no longer have similar incidents. The situation is still under investigation for proper handling.
On the evening of July 4, 2021, the Cyberspace Administration of China announced the removal of the “Didi Chuxing” app, citing violations of the “Cyberspace Security Law” and serious illegal collection and use of personal information. Didi Chuxing Technology Co., Ltd. was required to strictly abide by legal requirements, refer to relevant national standards, seriously rectify the existing problems, and effectively protect the personal information security of users.
![Didi monitors the 24-hour car usage volume of the Ministry of Natural Resources through big data.]Therefore, it is necessary to establish a sound access system. For the collection, storage, and commercial use of data for intelligent connected vehicles, it must be recorded and managed by relevant national departments, strengthen data privacy protection, and establish corresponding review systems. Intelligent connected vehicle companies have the obligation to inform users of possible privacy risks and give users the freedom to choose when collecting, using, transferring, or deleting data.
Data Ownership
Currently, regulatory authorities, law enforcement agencies, and companies all have the right to legally use vehicle data, and consumers also have the right to know the driving data of their own vehicles. However, the question of “who owns these data” is still a complex issue.
Why is the ownership of vehicle data a complex issue?
Vehicles not only integrate a series of complex systems, but also integrate different sensors. As long as a vehicle is driven, data can be collected on the surrounding environment and road conditions. Every car on the road becomes a “data black hole,” absorbing the surrounding environmental data. The direct consequence of this is that the owner of the car can obtain vehicle ownership when buying a car, but ownership alone is not enough for the vehicle to drive on the road. The car owner also needs to obtain various software and application aids, which in turn requires authorization to use.
Traditionally, buying a car was a one-time transaction, but now buying a car is gradually becoming a long-term service contract relationship. From the perspective of legal relationships, a car may involve multiple parties such as the owner, 4S shop, car factory, cloud service provider, telecom operator, passengers, and pedestrians, and different legal relationships and data flows connect different entities. Even the remote upgrade and maintenance of the vehicle itself (OTA) has huge differences from traditional recalls and 4S shop maintenance.
Then, who should own the data?
Mr. Li, the husband of the woman who submitted a roof claim against Tesla, believes that driving data is personal property and personal privacy. Tesla’s unauthorized disclosure to the media and the public without the owner’s permission infringes on personal privacy rights and consumer rights.
Chen Wen, director of the Digital Economy Research Center at the School of Finance of Southwest University of Finance and Economics, believes that the ownership of personal data information belongs to individuals, but there are difficulties in defining ownership in practice:
First, personal data information has storage costs. Companies or operators often store valuable data due to commercial considerations, and these data constitute an organic part of the company’s “core assets”.
Second, personal data has the property of social networks, particularly in the internet era, where personal data often blends with others. If data is fully attributed to an individual, there may be a suspicion of infringing on the privacy of others.## The difficulty of determining the boundaries and content of rights through established legal methods is a problem worldwide, due to the fact that data is often a combination of multiple stakeholders and interests.
For example, for consumers, there are personal information about the driver’s driving and riding; for car companies, it may include a large amount of data collected to maintain the safety of car operations and improve autonomous driving efficiency; for governments, cars also collect information about the road and surrounding maps, roads, and other information during the driving process.
Because of these characteristics, simply saying who the data belongs to cannot solve multi-interest conflicts. Even if ownership is determined, it cannot solve the content issue of rights and cannot distinguish which party should be protected in the event of a conflict.
Scholars generally believe that personal information belongs to individuals. But the problem is that data involves multiple stakeholders with multiple interests. Even if their respective ownership is determined, the key question of “whose rights have a higher priority” remains unanswered. Perhaps the key to the problem is not the ownership of the data, but how to exercise rights.
Laws and regulations related to data security
Behind the global surge in legislation, everyone is gradually realizing that whoever falls behind in legislation will be in a passive position in the digital era. The security and supervision of autonomous driving data have been raised to an unprecedented height of importance.
From China’s “Cyber Security Law,” “Measures for Security Assessment of Personal Information and Important Data Export (Draft for Comment),” “Measures for Security Assessment of Personal Information Export,” “Information Security Technology-Personal Information Security Specification,” “Measures for Security Assessment of Personal Information and Important Data Export (Draft for Comment),” “Action Plan for the Development of the Connected Car (Intelligent and Connected Vehicles) Industry,” “Personal Information Protection Law,” ” Data Security Law,” to many domestic and international regulations and policies such as the US “Autonomous Driving Act,” the EU’s “Intelligent Automobile Network Security and Adaptability,” and Germany’s “Road Traffic Law,” all have put forward requirements for data security from different perspectives. This means that all kinds of data generated and involved in the development of the autonomous driving industry need to comply with relevant legal provisions.
Currently, these related laws and regulations have comprehensively constructed the legal framework for information and data security.
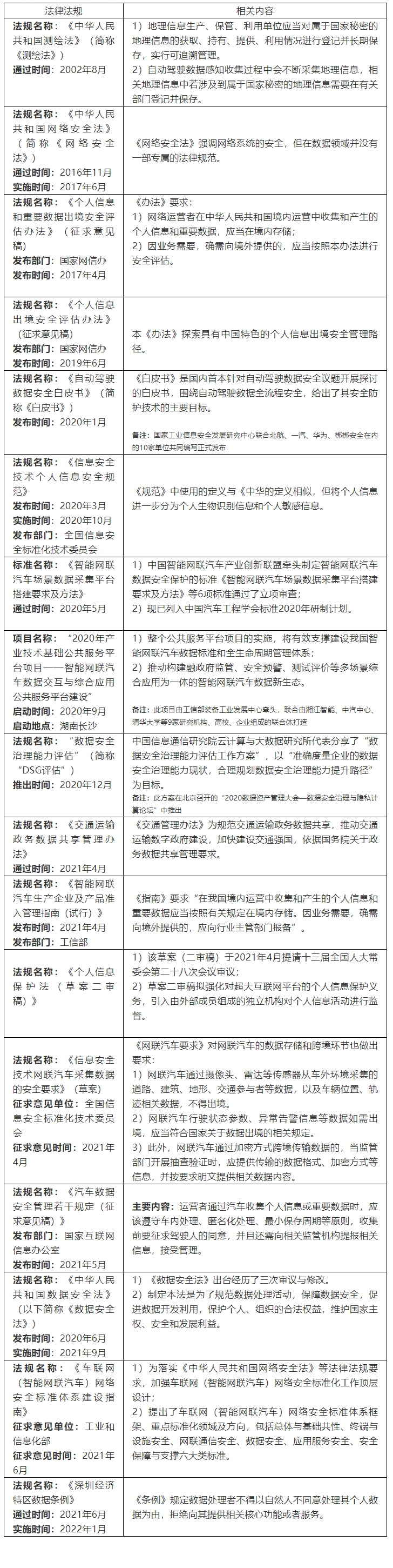
Domestic laws and regulations related to data security
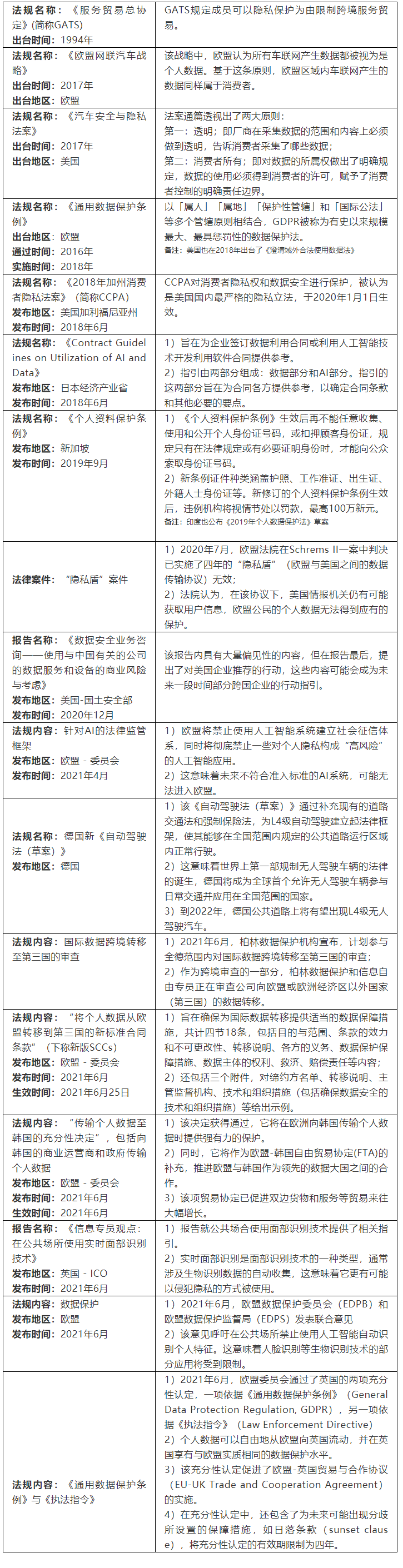
Foreign laws and regulations related to data security
This article is a translation by ChatGPT of a Chinese report from 42HOW. If you have any questions about it, please email bd@42how.com.