Author: Zhu Yulong
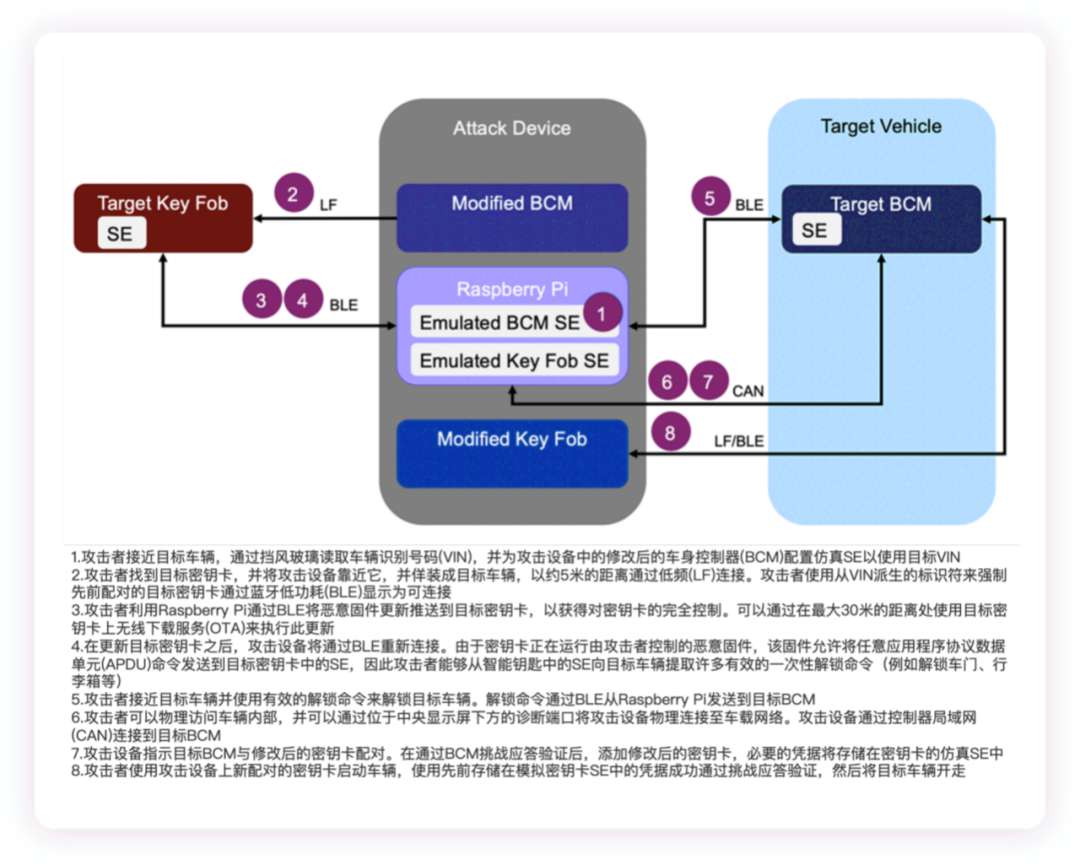
I’ve previously written about Tesla’s security system, “PET Key Reading and Anti-theft System of Tesla Model 3.” Recently, there was an interesting news in which Sultan Qasim Khan, a member of the UK information security company NCC Group, claimed that by using communication deception attacks, it’s possible to crack the Security system, unlock the vehicle and steal cars of Tesla Model 3 and Model Y. The method is similar to what was previously discussed; a disguised device is placed within 15 meters of the owner’s smartphone and key, and an application specifically designed for Bluetooth development kit on a laptop is used. Once the camouflaged relay device is successfully set up, the attack can be completed in “10 seconds” only. Hackers implement the aforementioned operation by forwarding communication using small hardware devices which is essentially similar to the attack on Model X previously.
Three Types of Driving Modes Supported by Tesla’s Security System
Tesla’s vehicle is mainly equipped with three types of keys for opening and closing: authenticated smartphones, key cards, and remote keys.
- Authenticated Smartphone (Setting a personal smartphone using Bluetooth to communicate with the vehicle)
This key supports automatic lock and unlock and other mobile app functions. The authenticated smartphone is the preferred key and doesn’t need to be taken out.
- Key Card
This uses short-range radio frequency identification (RFID) signals to communicate with the vehicle.
- Remote Key
This accessory is sold separately and uses traditional remote key with Bluetooth communication, and features an Ultra Wideband (UWB) function for passive entry. When the key approaches the vehicle, the door handles will support it. A total of 19 keys are supported by the car, with a maximum of four remote keys.
Currently, Tesla’s main control system mainly includes the following:
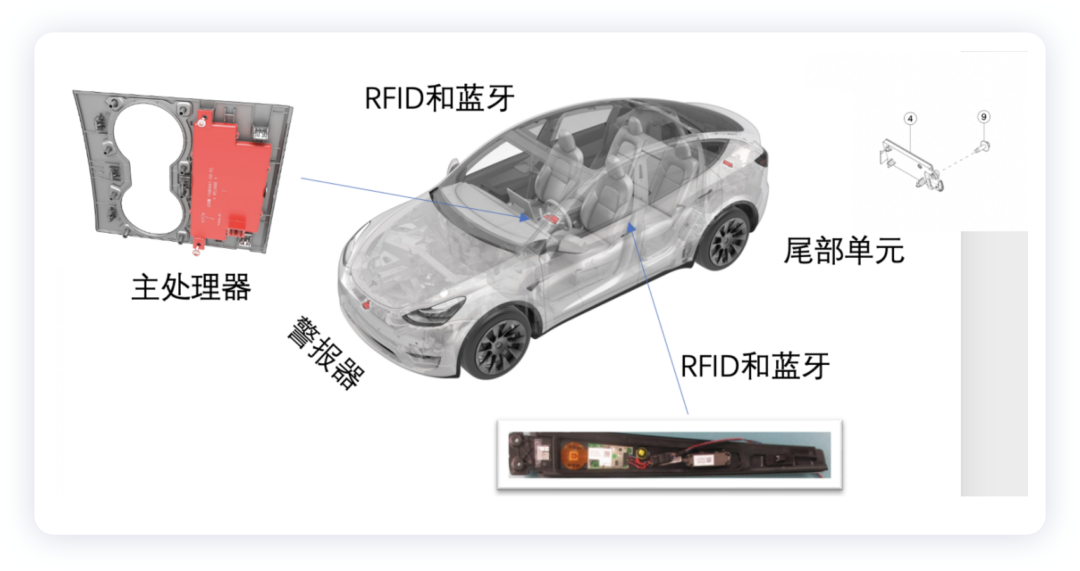
Within this:
- Security ECU
Separated from the original BCM, it’s a single main control phone with three BLE units of signals, and RFID is confirmed through a CAN signal.
- BLE B-Pillar
RFID recognition card, supports Bluetooth and UWB, one way CAN.
- BLE Rear
Added UWB chip, mainly used for Bluetooth and positioning, one way CAN.
Power supply is considered from the position of the body here.
Design Details
Here, we will start by talking about several relatively simple systems, beginning with the Security ECU.
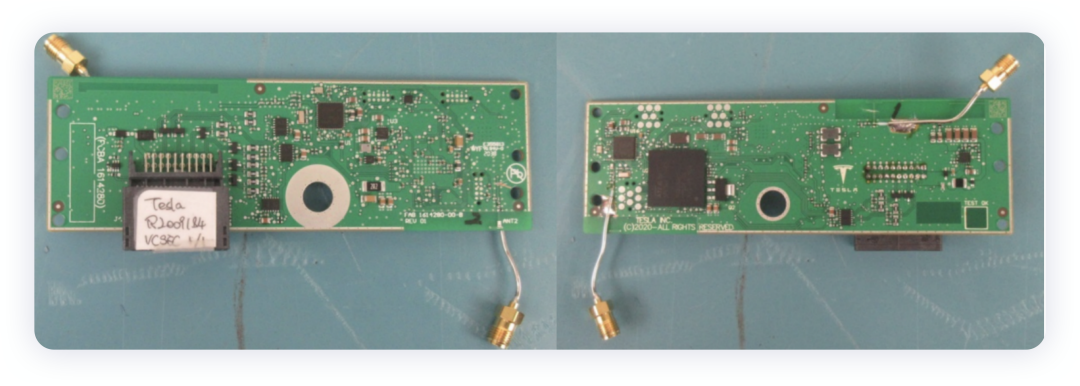
- Security ECU
Compared with the previous generation, the overall PCB size of this controller has been optimized. In particular, the PCB antenna has been changed from the original design to an independent antenna, and the 13.56MHz design has been eliminated, and some adjustments have been made to the chip.
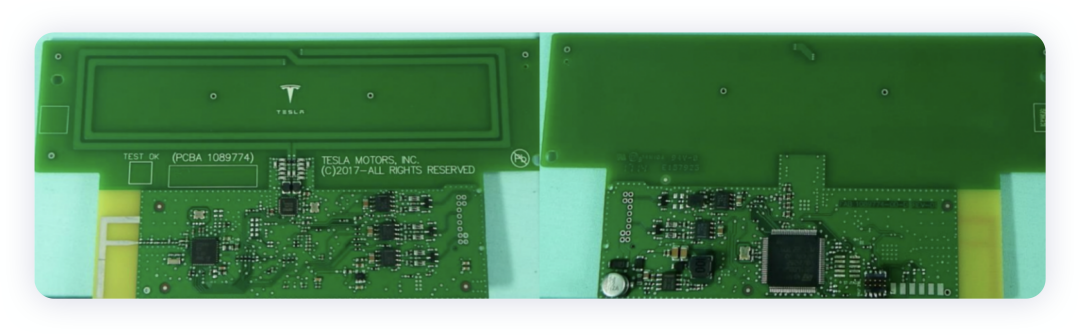
- B-pillar controller
This controller is mirrored and supports card reading on both the left and right sides, with support for 13.56MHz, 2.4GHZ, and 6.5-8GHz UWB.
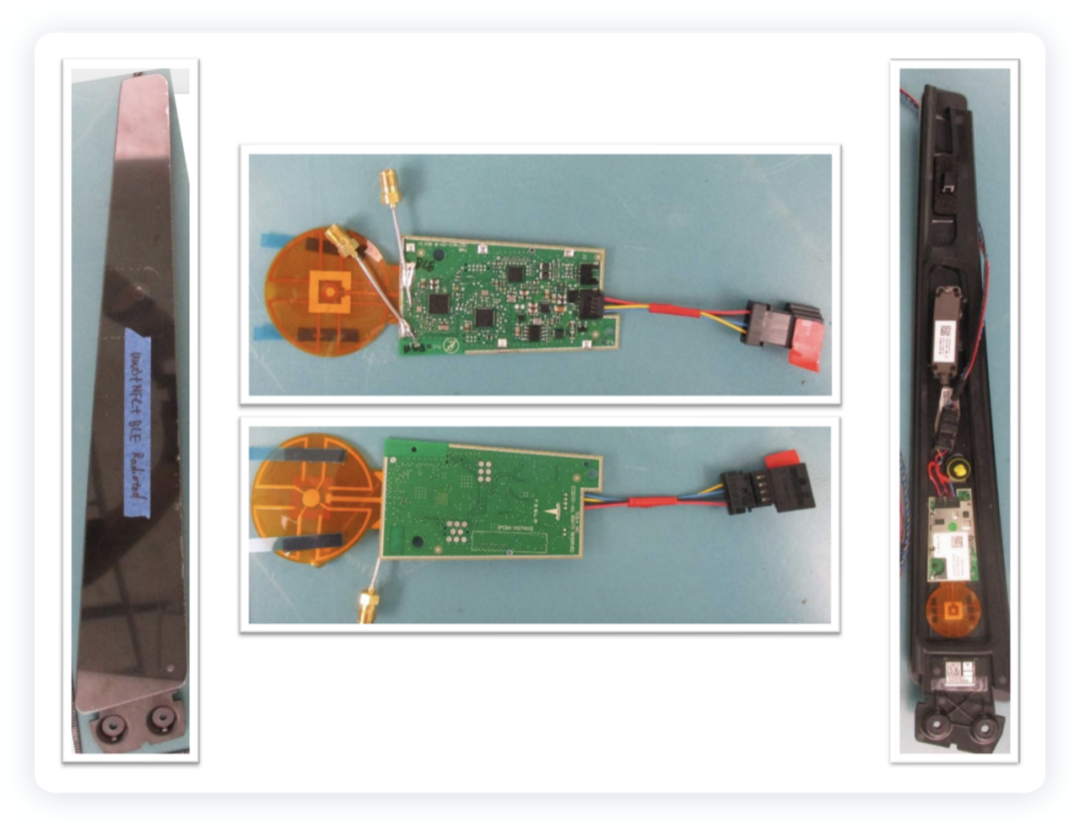
- Tail-end Bluetooth controller
Looking at this controller, it is also particularly simple, centered around TI’s 2642 Bluetooth MCU, with the addition of a CAN communication chip and a power supply unit, as well as a UWB chip.
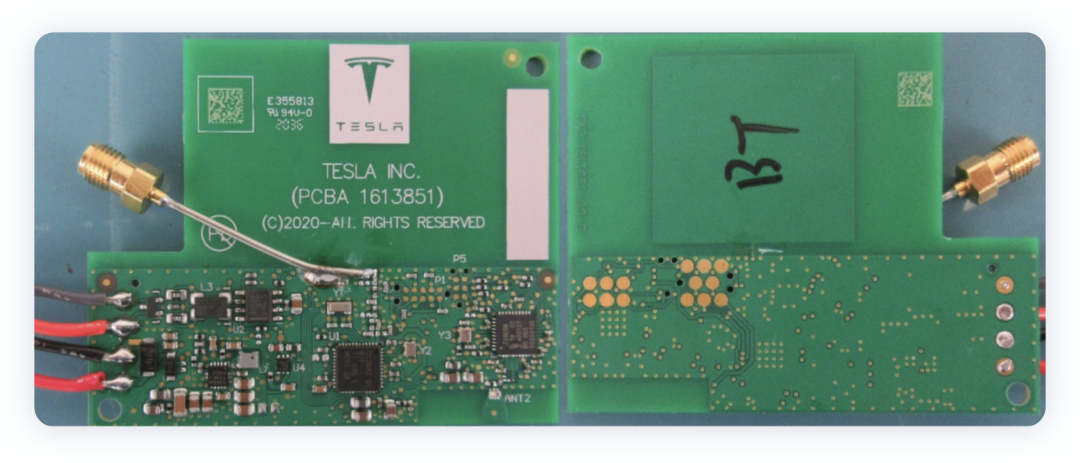
These controllers bundle communication and MCU functionality, so after you call it a controller, it will inevitably evolve into an intelligent unit.

Summary: This method of cybersecurity attack is actually quite interesting, and in terms of the system design, it can be replicated in the future. I think the systems based on Bluetooth and UWB strike a good balance between ease of use and security.
This article is a translation by ChatGPT of a Chinese report from 42HOW. If you have any questions about it, please email bd@42how.com.
