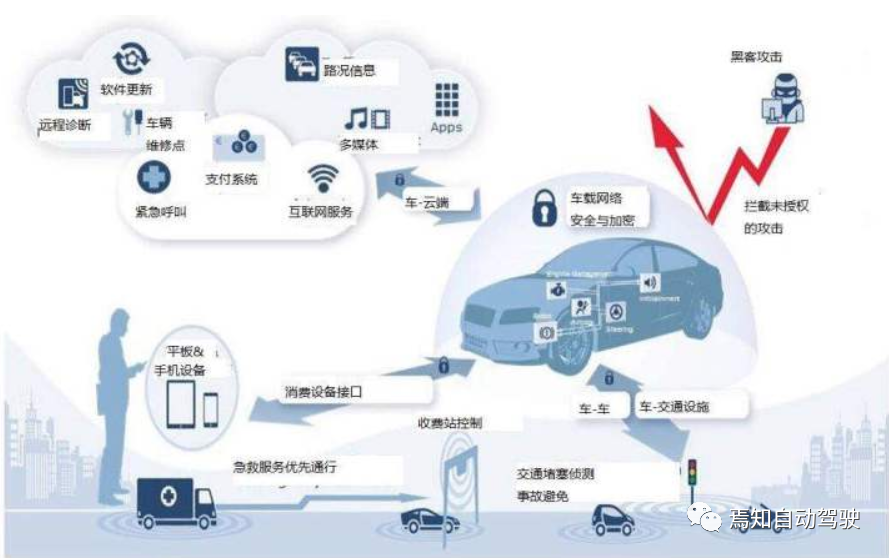
As the level of automation in vehicles increases, security measures to protect vehicle functionality should defend against unauthorized access and manipulation to ensure the safe and secure operation and integrity of the vehicle, its components, and its functions, especially its vehicle control function. Ensuring the highest safety standards and protecting vehicle safety in the best possible way is fundamental to maintaining the sustainable expansion of automated driving functions, while taking into account the latest technological level.
Why does information security occupy such a high position in the overall safety of the automated driving system?
Due to the extreme connectivity between the automated driving vehicles and their operating environment, new challenges are presented in terms of information security in automated driving. These challenges range from meeting regulatory requirements, ensuring design safety, to protecting cars and customers from network security attacks. The interconnectivity of information increases the attack surface between the control functions of connected vehicles, IT back-end systems, and other external information sources. This rich attack surface has attracted malicious actors with various goals. In short, we have developed to a level where ensuring the safe operation of vehicles is of utmost importance. This process should adopt network security principles and practices to ensure attackers cannot arbitrarily control the driving state of the vehicle, and attacks are difficult to expand to the degree of simultaneously utilizing multiple vehicles.
The focus of this article is on network information security, analyzing the challenges that current mainstream automated driving systems face in terms of network information security based on the latest admission guidelines. At the same time, by providing some examples, it illustrates the additional components, external information, and external interfaces required to achieve automated driving function information security.
When expanding from L2 vehicles to L3 or L4 vehicles, the challenge of network security is that automated driving functions heavily rely on external data, sensor information, maps, location information, etc. If the integrity or authenticity of this data is compromised, the blocks of the automated driving functions (perception-planning-decision) will use erroneous data to manipulate the vehicle, which may cause inaccurate control or even driving to other places that deviate from correct operation. If automated driving cars are attacked, the impact will be even greater, as people inside the car will not be able to control it in a timely manner. Therefore, effective network security measures should be fully introduced to protect automated driving from malicious actors.
 # Security Measures for Building Resilient Autonomous Driving Systems
# Security Measures for Building Resilient Autonomous Driving Systems
This section discusses the methods to address the aforementioned threats. The process to build secure autonomous driving systems, which can withstand attacks, is described first. This process requires information security design to be applied to the system to achieve coverage in any abnormal state. A strict and fully integrated information security analysis process forms the basis for developing secure autonomous driving systems. This process helps to tightly integrate various security controls, which will be introduced after this process. Defense in depth is usually adopted in information security methods to ensure that controls are layered throughout the system, which prevents relying solely on the periphery to defend against attacks.
Information Security Development Cycle
The Security Development Lifecycle (SDL) is the process for establishing information security. Specifically, the SDL stipulates security measures to be taken in specific stages during the development process. These practices are diverse and aim to actively prevent attacks or detect and fix vulnerabilities as early as possible. The SDL is tailored for each part of the development process to adapt to product development and product maintenance. Using these lifecycles ensures a structured approach to proactively address security issues during the development process.
No matter which development process is used, SDL generally categorizes practices into three types:
The first is development and maintenance, which includes effective training to ensure that the process of creating knowledge baselines, policies, procedures, and guidelines within the development organization has the required foundation. Development includes recognized practices in software engineering, such as information security requirement definition, threat modeling, static and dynamic analysis, fuzz testing, code review, and penetration testing. Finally, maintenance measures include event response, update signature procedures, and other practices to ensure that the product continues to operate after release.
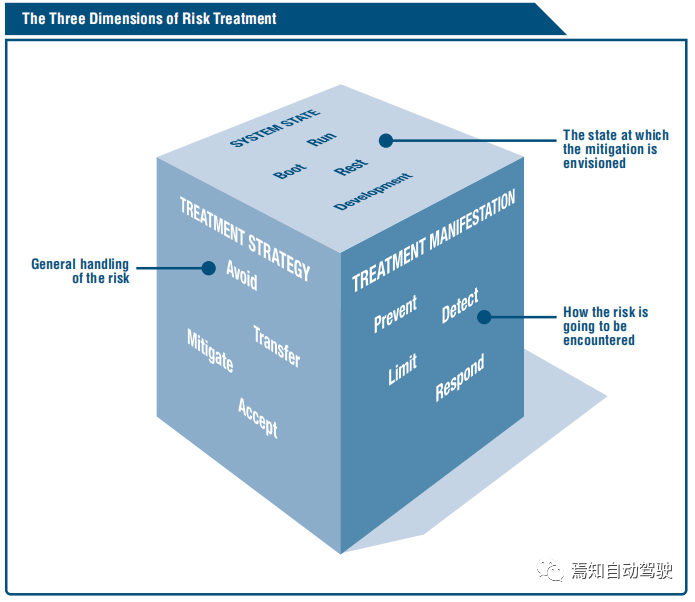
When applying various SDL practices, many trade-offs need to be made. Risk assessment is used to help determine where limited resources should be allocated and how to prioritize methods. At least three dimensions are important when considering compromises during the development process, as shown in the diagram below: system states, risk treatment strategies, and risk treatment performance.
① System states help to define appropriate mitigation measures;
② Risk treatment strategy provides options for handling risks (e.g., avoiding, transferring, mitigating, or accepting risks);
③ Result performance helps to understand how the selected method changes the risks produced and the effects brought about.
Defense in Depth Security Architecture
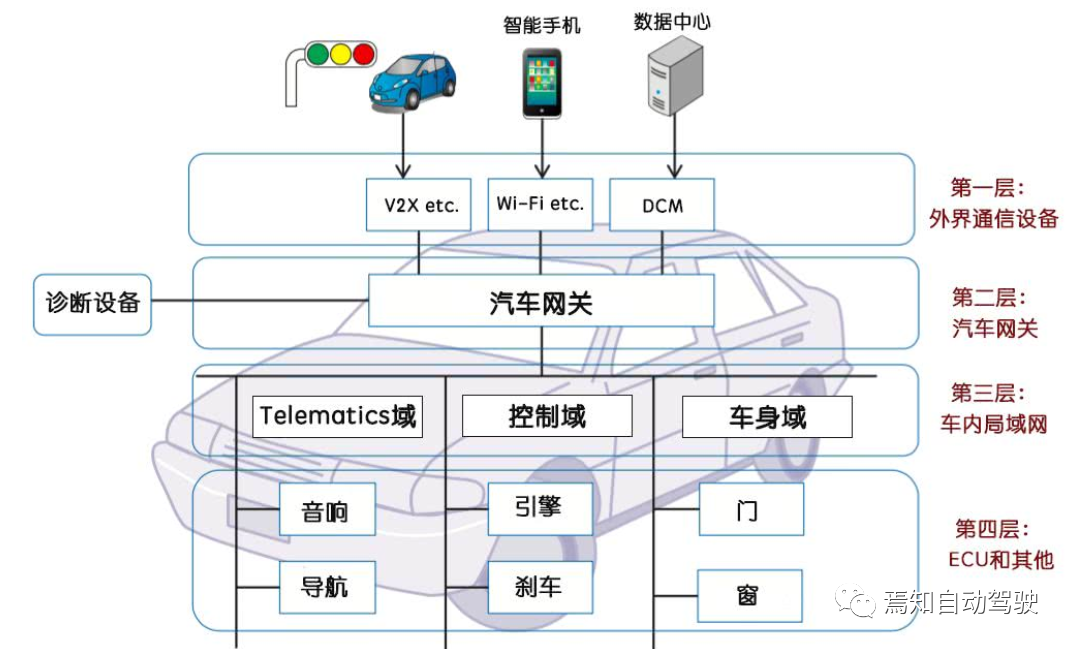
This section discusses how to layer autonomous driving systems to achieve the security goals discussed earlier. For autonomous vehicles, defense in depth begins with low-level components and continues up to individual devices, forming device groups that can identify the system (e.g., perception), the vehicle itself, and the infrastructure required to support the vehicle.To achieve the goal of automotive safety, embedded autonomous driving systems mainly consider the confidentiality, integrity (including authenticity and availability) of data, (sub)systems, functions, or components as the traditional information security triad. At the component level (e.g., microcontrollers, ECUs, camera sensors, etc.), primitives can be used to safely achieve confidentiality, integrity, and authenticity. This typically means ensuring that microcontrollers are integrated perfectly with dedicated hardware like hardware security modules or similar, and building advanced functionality with encryption capabilities used therein. Meanwhile, the functions of component tamper-proofing, configurability (e.g., removing or disabling unnecessary functionality), and upgradability are also taken into account.
By moving up one level, a secure input device unit (e.g., LIDARS, radar, video, etc.) is established by utilizing components. At this point, it is necessary to determine the integrity and authenticity of firmware and software security boot, encrypt and authenticate messages, and authenticate entities authorized to update devices and updates themselves. At the same time, alleviate denial-of-service attacks carried out against devices and prevent devices from accidentally leaking information. When devices form a system, it becomes important to ensure secure group communication, prove the device status to the rest of the group, and resist the function of denial-of-service on shared communication channels. The methods used at this point benefit from redundancy used for security. By using sensor fusion and cross-referencing the perceived content in multiple ways, attackers are forced to coordinate their attacks on multiple different devices to deceive the entire system. Independent secure redundant systems in vehicles further contribute to defense in depth, because an attack on one system does not necessarily change the operation of another independent system.
Intelligent connected vehicles (V2V) are usually supported by public (e.g., DSRC, GNSS, etc.) and private (e.g., logistics department) infrastructure. Although autonomous driving vehicles consider receiving data from infrastructure, especially data that can be strongly authenticated, these vehicles ultimately maintain their own decision-making authority, rather than infrastructure. At this point, many related personnel involved in autonomous driving vehicles (such as operation, management, maintenance, etc.) are also considered, so human access to vehicles is limited and separated. For example, the operator may need to access the location and status of the vehicle without knowing who is in the vehicle.
All of these measures improve the safety, reliability, and trustworthiness of L3 and L4 vehicles. Some security control examples that help achieve the above security goals are listed in the following table.
| Security Controls Examples |
|---|
| Authentication and authorization |
| Integrity protection |
| Confidentiality protection |
| Anti-spoofing measures |
| Availability protection |
| Tamper-proof measures |
| Configurability |
| Redundancy and fail-safety |
| Privacy protection |
| Secure update mechanism |
| Security monitoring and situational awareness |
Improving Information Security Performance Based on the “Autonomous Driving Access Guidelines”The latest access regulations for autonomous driving clearly specify multiple provisions regarding network security, limiting the network security abilities required during driving from different dimensions, primarily involving three aspects of building:
-
Guaranteeing enterprise network security abilities, including network security responsibility, technology, protection, monitoring and warning, emergency response, vulnerability management, data security management, vehicle network card real-name system, supply chain security, auditing standards, after-sales supervision, change, technical support, and assistance.
-
Guaranteeing intelligent connected vehicle product network security during development, involving risk assessment, concept design, product development, and testing verification, ultimately requiring asset identification and risk assessment, providing design requirements and detailed design specifications.
-
Demanding enterprise self-testing abilities for vehicle network security testing, providing corresponding verification test reports.
For the sub-items involved in the aforementioned information security design abilities, it is necessary to combine intelligent connected vehicle information security access requirements and ISO/SAE 21434 standard requirements to establish a vehicle networking information security management system throughout the entire lifecycle, and gain full access approval based on sufficient conditions. This includes supporting organizational management and supplier management under the target state and the content of automotive products in the concept, design, research and development, production, operation, maintenance and scrapping stages.
As indicated in the information security management system shown in the figure above, the overall automatic driving information security level needs to establish corresponding abilities from the following three levels to cover as many product access security requirements as possible:
-
Satisfying automatic driving information security compliance requirements, that is, according to actual enterprise conditions, with the goal of meeting compliance requirements, assisting in the implementation of the intelligent connected vehicle information security management system plan, and preparing for automotive information security system certification.
-
Strengthening internal control mechanisms to ensure business continuity, establishing and improving automotive information security processes and systems, and strengthening process management. According to the system, strengthening the management and coordination of automotive overall information security work, and ensuring the implementation of the system.
-
Further optimizing and improving existing process specifications, optimizing and improving the existing security management system to adapt to the continuous development of intelligent connected vehicle information security.
From the perspective of the entire product design level, it is necessary to fully achieve “autonomous and controllable” in the research of relevant information security for autonomous driving products.
- Establish an autonomous and controllable information security protection system. Component protection includes lightweight encryption, ECU trusted boot, firmware trusted loading, etc., covering data security, message security, privacy security, and application security for the entire vehicle and cloud services. Starting from numerous parts of the entire vehicle, carry out targeted protection and protect component information security in all aspects.Translate the Chinese Markdown text below into English Markdown text, in a professional manner, preserving HTML tags inside Markdown, output only the results.
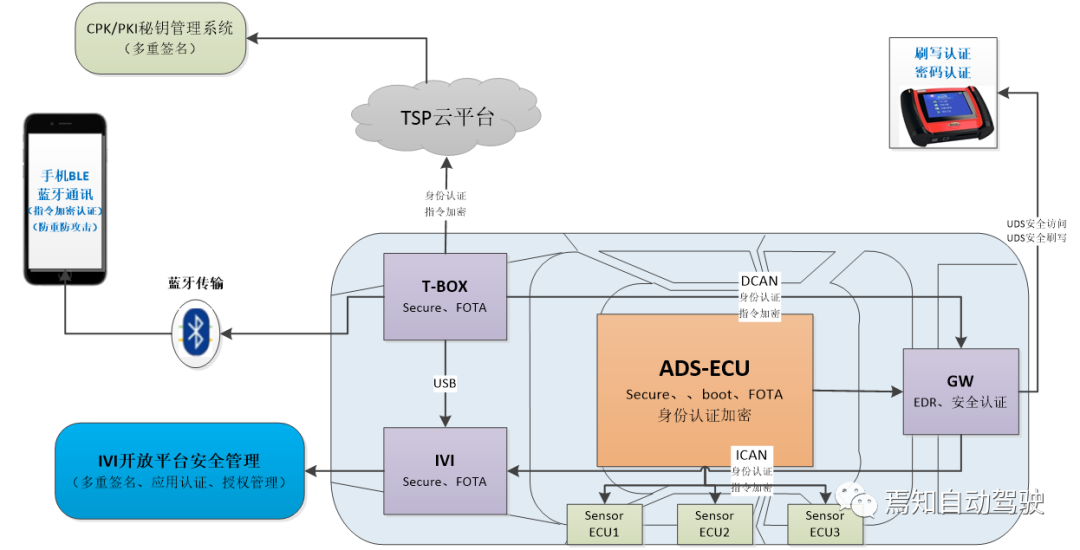
- Establishing an independent and controllable information security testing platform
The automotive information security attack and defense penetration platform integrates a security testing system that can complete the information security verification of vehicle systems, connected car systems, and autonomous driving systems.
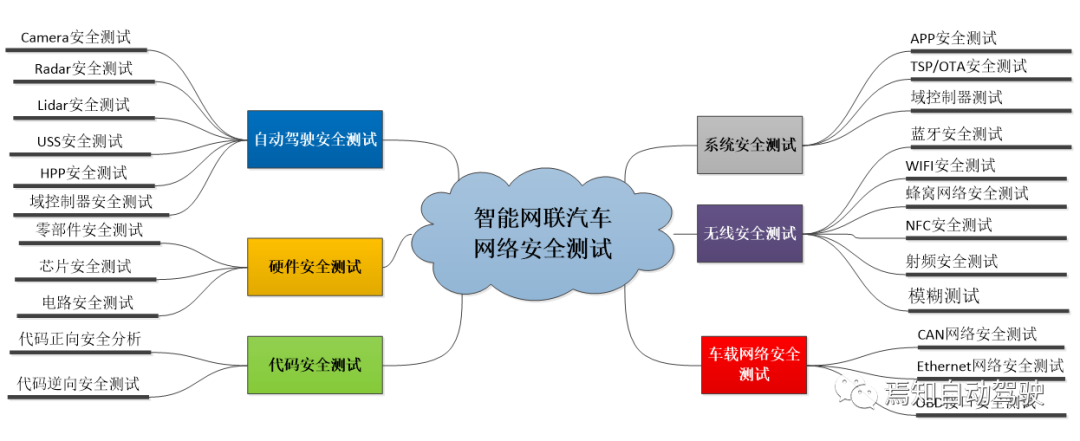
- Building a trusted network support system for connected cars
Construct an automotive industry-connected car network trust support platform to build an industry-standard connected car communication identity authentication system, supporting the application of two kinds of certificates, V2X CA certificate and X509 certificate, in different scenarios. Currently, in accordance with the relevant standards of the national electronic certification service, a high-standard computer room has been constructed and deployed, and the China automotive industry-connected car network trust support platform has been launched.
Conclusion
Currently, the automotive industry is undergoing a profound transformation period, and intelligent connected vehicles provide consumers with convenient usage, rich application content, and secure driving environments. But at the same time, the information security issues brought about by intelligence and connectivity face multiple risks. Information security is the premise and guarantee for the development of intelligent connected vehicles. Solving the information security of intelligent connected vehicles is the most critical link to ensure that they successfully pass the admission and travel smoothly on the road.
This article is a translation by ChatGPT of a Chinese report from 42HOW. If you have any questions about it, please email bd@42how.com.